Some Known Details About Daas Desktop As A Service

Actually, under the hood of most Daa, S offerings is really a VDI service. Due to the fact that VDI retains the majority of the underlying parts that are extracted in Daa, S, VDI is frequently considered a lot more hard to have from a technological perspective. There are, nonetheless, a couple of VDI services that have actually taken care of to streamline the procedures related to release and management, and also we'll be featuring one of those services later in this post.
Those that have this capability are less complicated to own as well as take care of, as this release choice eliminates the requirement to develop and take care of specific parts of the underlying facilities (e. g., physical servers, storage systems, networking, and also cooling systems, along with hypervisors, to discuss a few). From the viewpoint of the end user, there are no noticeable differences in between applications and desktop computers supplied by Daa, S and also those supplied by VDI.
Every Daa, S environment complies with a multi-tenant model. Definition, its resources are shared amongst multiple customers/organizations. On the various other hand, VDI atmospheres usually comply with a single-tenant model, wherein all sources in a VDI environment are consumed by a single organization. Some VDI services do have multi-tenant capabilities, the feature is made use of (by MSPs, for example) to deliver Daa, S to clients.
Not known Details About Daas Desktop As A Service
These responsibilities are all taken in by the Daa, S carrier. It's the exact reverse for VDI consumers, who must organize all these duties. As noted earlier, there are VDI services that can be released in the cloud. For these deployments, a substantial portion of the infrastructure-related obligations (e.
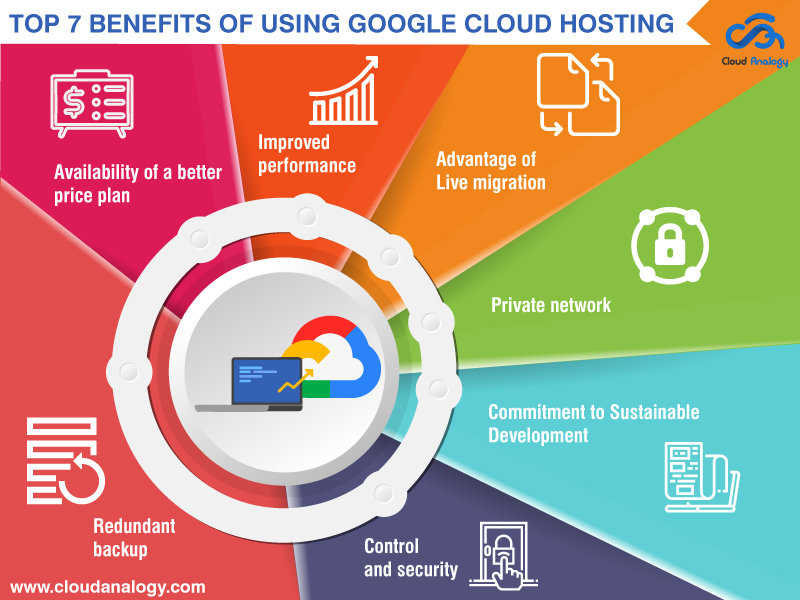
Nevertheless, deployment, administration, and also upkeep of the VDI control plane is maintained by the consumer. As with all cloud-based services, Daa, S costs are based primarily on running expenses (OPEX). By contrast, VDI prices are based primarily on capital investment (CAPEX). This implies that Daa, S customers are extra worried with continuous costs, while VDI consumers are extra worried with upfront costs.
It's different in a VDI environment released on-premises where, for instance, your IT manager might understand exactly which rack your VDI service is running on or which storage space device holds your most confidential documents. Daa, S settings are simply like any type of cloud environmentthey're highly scalable. You can he said increase and acquire your fleet of virtual desktops on-demand with convenience.
The Best Strategy To Use For Daas Desktop As A Service
Although the VDI remedy itself could be scalable, that scalability can be restricted by the underlying physical framework (i. e., physical web servers, storage space systems). Now that you recognize the key differences in between Daa, S and also VDI, let's speak about their advantages, negative aspects, and the usage cases they're each best matched for.
Daa, S has numerous benefits. It provides: Daa, S acquires all the advantages of cloud computing. That includes having a high degree of scalability. Daa, S atmospheres can be rapidly broadened and also contracted depending upon need. You do not have that scalability with VDI. That's why, before developing your VDI atmosphere, you require to forecast possible peak need in order to build the appropriate capacity.
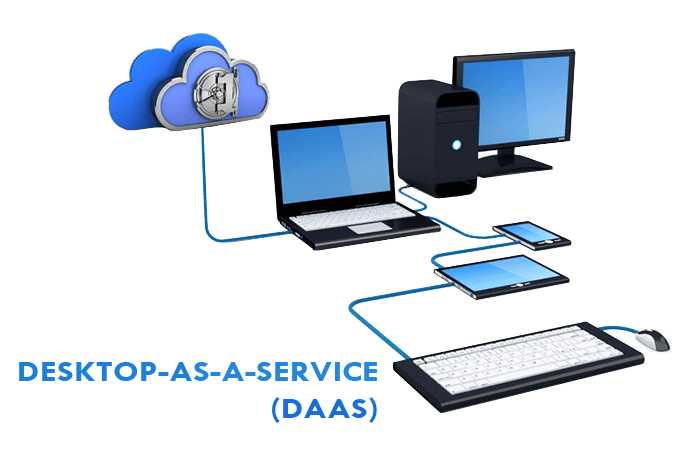
Not known Incorrect Statements About Daas Desktop As A Service
— Cloud Links (@ldcloudlinks) December 14, 2022
official statement
Although the mass of your expenses are concentrated in the structure phase of your VDI infrastructure, it does not mean you can not sustain extra prices in the future. Some expenses, such as those for equipment replacements or repairs, can come when you least anticipate them. In Daa, S's subscription-based billing design, prices are much more foreseeable.

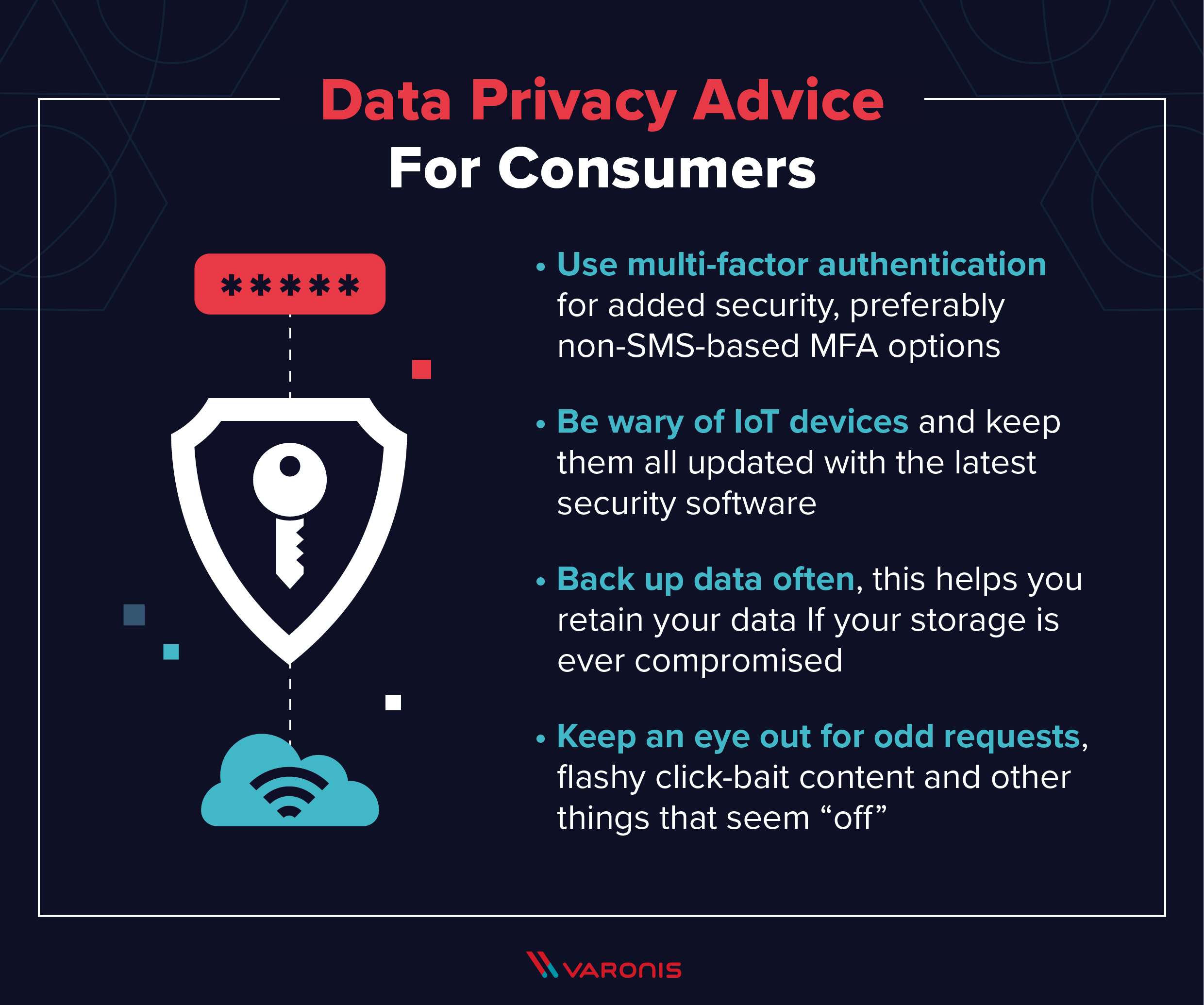
This can make budgeting easier. Daas additionally has some downsides such as: Although Daa, S suppliers have network segmentation and also data seclusion procedures check here in position, the multi-tenant design of Daa, S atmospheres (where multiple companies share the underlying infrastructure) still makes them rather vulnerable to information leakages. This can be triggered by unintentional and also intentional negligences such as an overallocation of benefits by a cloud designer, a misconfiguration by an organization's cloud administrator, or a malicious side movement by a danger star (DAAS Desktop as a Service).
A Daa, S setting's OPEX-based expenses mean you must deal with ongoing expenditures that, in the lengthy run, can end up being much more pricey than the ahead of time expenses plus the operational prices of a VDI environment. Since Daa, S atmospheres are operated as well as administered by the service carrier, you do not have as much control over your digital assets (e.
Daa, S providers, carriers the particularly cloud providers, carriers several carry out security measures safety and security can help guarantee the ensure of safety and security digital assetsElectronic
When a sudden rise sought after asks for mass hiring of momentary workers, it's much easier to accommodate those momentary hires with Daa, S because if a VDI setting's underlying infrastructure is already at optimal capacity, you'll be compelled to add even more physical web servers. What will you finish with those web servers when the need subsides? For Daa, S, it's just a matter of momentarily adding more registrations while the need exists.